Data Flow Diagram For Security Architecture Security Event L
What is security architecture diagram Data flow: creating a bbm enterprise conference Data flow diagram of smart security framework
Network Security Diagram
Iot & enterprise cybersecurity Physical structure of data security system for a small business Database process flow diagram
Network security model
Network security diagram firewall wireless computer wan diagrams secure lan architecture networks example networking drawing between clipart conceptdraw system cyber[diagram] architecture diagram in data guard Storage area networks (san). computer and network examplesMicrosoft graph security api data flow.
Security architectureFlow data diagram security level dfd system visit yc examples network Network security modelData flow diagram.

Security architecture software network components development tutorials tutorial
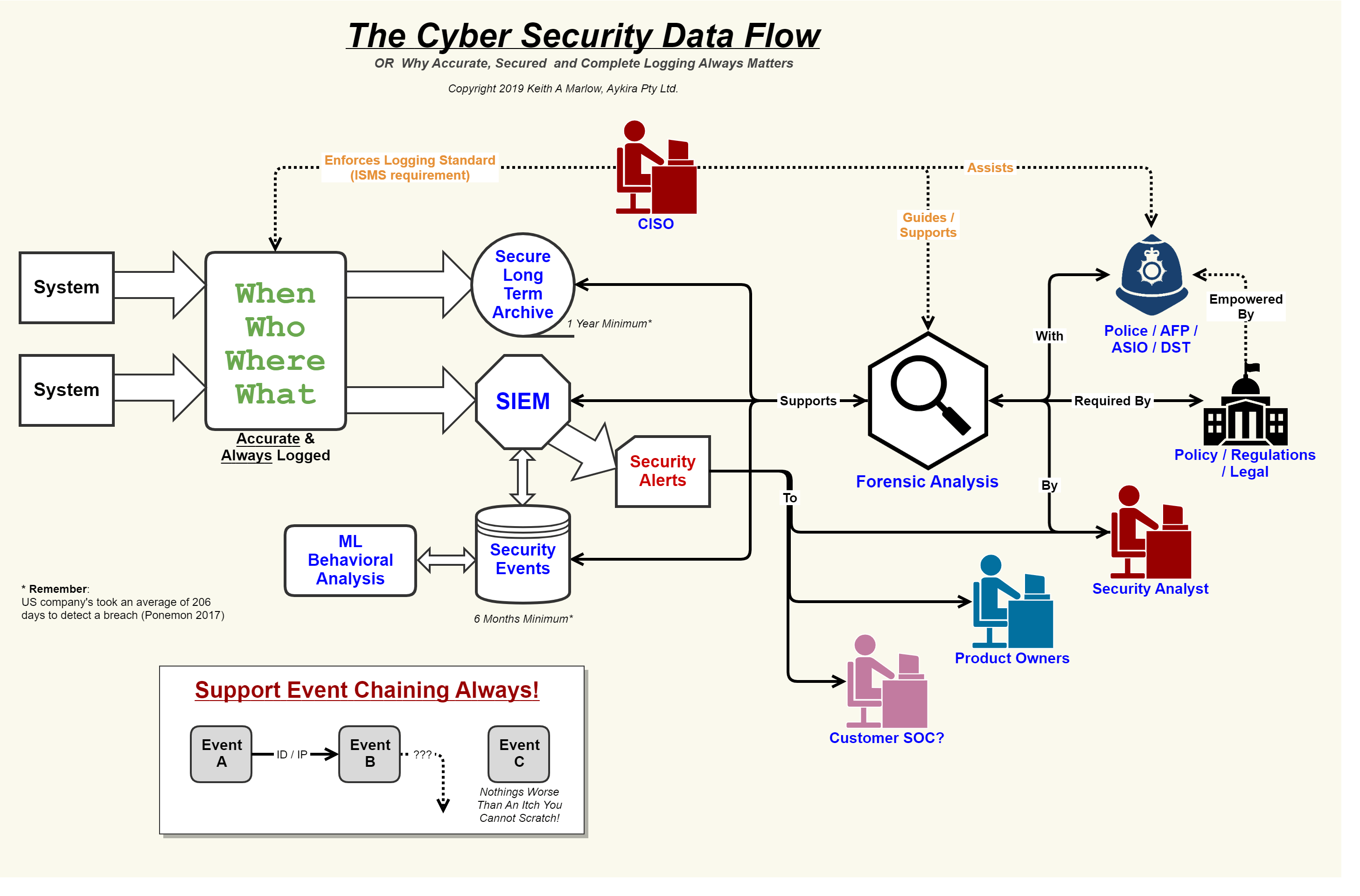
Security event logging, why it is so important – aykira internet solutionsYour guide to fedramp diagrams Architecture cybersecurity enterprise iot cyber security diagram system softwareIso27001 isms information security architecture overview.
Data flow diagramComptia network+ tutorial: module 05, part 04: wireless network threats Network security diagramThe following data flow diagram template highlights data flows in a.

Security flow data cyber event logging diagram internet logs important why so together showing concerning events au putting
What is data security?Data flow and security overview Security event logging, why it is so important – aykira internet solutionsData flow kaavio symbolit, tyypit, ja vinkkejä.
Security network diagram control computer diagrams devices networks secure access encryption solution cloud examples model architecture example conceptdraw software systemData flow diagram Security flow cyber data event logging diagram logs internet important why so together putting events auNetwork security diagram firewall wireless computer diagrams wan example secure architecture lan networks networking clipart between devices conceptdraw drawing system.

Security network diagram architecture example diagrams firewall computer cyber microsoft clipart conceptdraw networks recommended model draw secure examples management flowchart
Network security diagramsSecurity network diagram control computer devices diagrams networks access solution encryption secure examples model architecture conceptdraw example cloud area software Security architecture, enterprise architecture, knowledge managementData flow diagram in software engineering.
Security network diagram model cloud diagrams government computer solution devices conceptdraw example access networks architecture solutions cybersecurity information models examples .